Data Privacy & Ethics: Challenges and Solutions
Data Privacy: In the dynamic landscape of digitization, businesses face myriad challenges in safeguarding their most precious asset—data. This BugBounter blog post explores the critical intersection of data privacy and ethics, shedding light on the challenges faced by businesses and offering strategic solutions to fortify their cybersecurity defenses. Read more.
Don’t feel like reading today? – Contact BugBounter for learning more about data privacy & ethics, and how can we help you.
The Evolving Landscape of Data Privacy Laws

Recent years have witnessed a seismic shift in global data privacy laws, with governments and regulatory bodies taking proactive measures to shield individuals’ sensitive information. From the European Union’s General Data Protection Regulation (GDPR) to the California Consumer Privacy Act (CCPA), the regulatory landscape has become increasingly complex.
Data Privacy Laws in Numbers
- 1. GDPR has imposed fines totaling €292 million since its enforcement in 2018 (Source: GDPR Enforcement Tracker)
- 2. CCPA violations can result in penalties ranging from $2,500 to $7,500 per violation [Source: California Consumer Privacy Act (CCPA)].
Data Privacy Challenges and Pain Points: Navigating the Regulatory Maze
Amidst the complex web of regulations, businesses encounter numerous challenges and pain points. One of the primary struggles is ensuring compliance with diverse and ever-changing data privacy laws across different jurisdictions. The intricacies of these laws often pose significant operational hurdles, requiring businesses to invest considerable resources in staying abreast of the latest developments.
Bug Bounty Programs: A Strategic Imperative for Data Privacy Ethics
In response to these challenges, organizations are turning to bug bounty programs as a strategic imperative to bolster their cybersecurity defenses. Leveraging the collective power of ethical hackers, these programs enable companies to identify and rectify vulnerabilities before malicious actors exploit them.
But how bug bounty programs can be more advantageous compared to the traditional cybersecurity assessments such as penetration testing? – Find out below.
| Criteria | Traditional Cybersecurity Testing | Bug Bounty Programs |
|---|---|---|
| Identification of Vulnerabilities | Reactive approach: addressing vulnerabilities only after discovery. | Proactive approach: leveraging cybersecurity experts to find and fix vulnerabilities before exploitation. |
| Cost-Effectiveness | Higher costs associated with traditional testing methods. | Variable costs, decided by the program owner, based on rewards paid to cybersecurity experts, often more cost-effective in the long run. |
| Speed of Detection and Resolution | Time-consuming processes, delaying vulnerability identification and resolution. | Rapid identification and resolution of vulnerabilities, minimizing the window of exposure to potential threats. |
💡 Tip: Read another blog post by BugBounter for a more detailed comparison.
Bug Bounty Programs: A Pillar for Data Privacy & Ethics of Your Company
Bug bounty programs, often powered by cybersecurity experts, leverage ethical hacking as a proactive approach (see the table above to understand what do we mean by “proactive approach”) to identify vulnerabilities. This cybersecurity methodology not only aligns with the highest ethical standards but also addresses the challenges presented by the dynamic nature of data privacy laws.
Here are some statistical insights:
- 72% of organizations believe that bug bounty programs are “very” or “extremely” effective in identifying and mitigating security vulnerabilities.
- Bug bounty platforms have witnessed a 42% year-over-year increase in reported vulnerabilities.
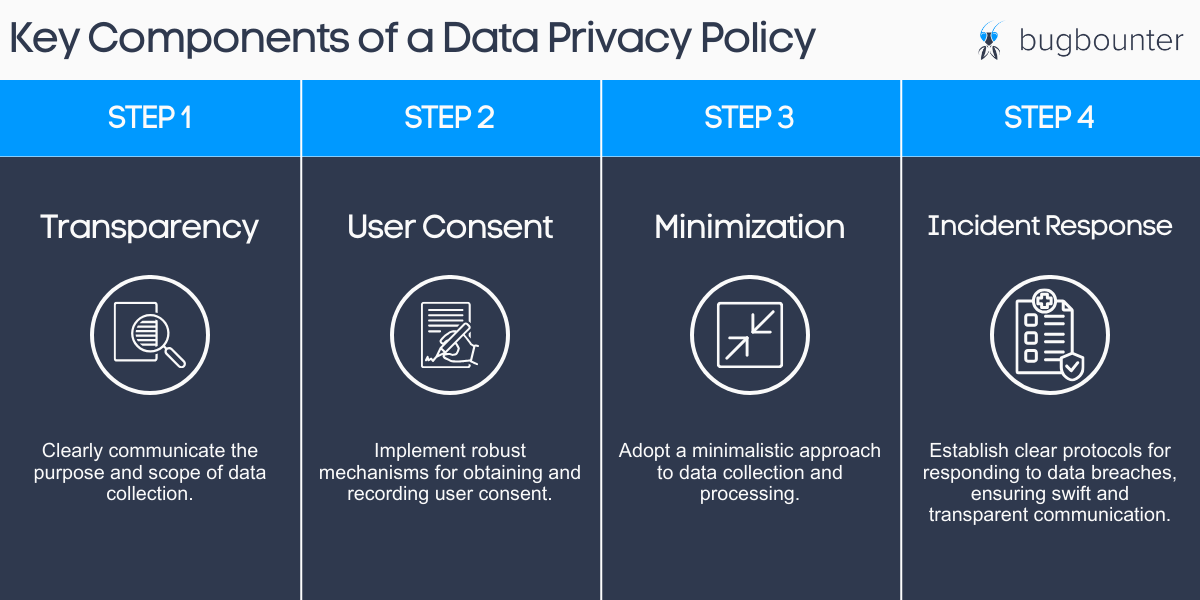
BONUS: How Can You Craft a Robust Data Policy?
While bug bounty programs play a pivotal role, a robust data privacy policy serves as the foundation for ethical data handling. Businesses must meticulously design and implement policies that address the challenges of compliance, ensuring transparency and accountability.
Here is a diagram for a clear explanation of the steps for a robust data policy:
Conclusion: Empowering Your Business with Bug Bounty
Data privacy is not just a legal requirement but a strategic imperative. Businesses that embrace bug bounty programs, coupled with comprehensive data privacy policies, are better positioned to navigate the challenges posed by an ever-evolving cybersecurity landscape. As we move forward, the symbiotic relationship between bug bounties and ethical data handling will be crucial in safeguarding not only sensitive information but also the trust of customers and partners alike.





