HomeBlog List
Recent Blogs

Payment fraud in eCommerce and retail industries
Explore the landscape of payment fraud in ecommerce and retail, learn about common types, and discover effective prevention strategies. Safeguard your business in the digital era with insights from bug bounty platforms.

Security in digital transformation: tech & challenges
Navigate digital transformation securely with insights on challenges, cybersecurity, and bug bounty benefits. Ensure success in the evolving tech landscape..

Why is executive leadership important for cybersecurity
Unlock the secrets to resilient cybersecurity leadership. Explore the pivotal role of executives in safeguarding your organization.

Subscribe to our newsletter

Payment fraud in eCommerce and retail industries
Explore the landscape of payment fraud in ecommerce and retail, learn about common types, and discover effective prevention strategies. Safeguard your business in the digital era with insights from bug bounty platforms.

Security in digital transformation: tech & challenges
Navigate digital transformation securely with insights on challenges, cybersecurity, and bug bounty benefits. Ensure success in the evolving tech landscape..

Why is executive leadership important for cybersecurity
Unlock the secrets to resilient cybersecurity leadership. Explore the pivotal role of executives in safeguarding your organization.
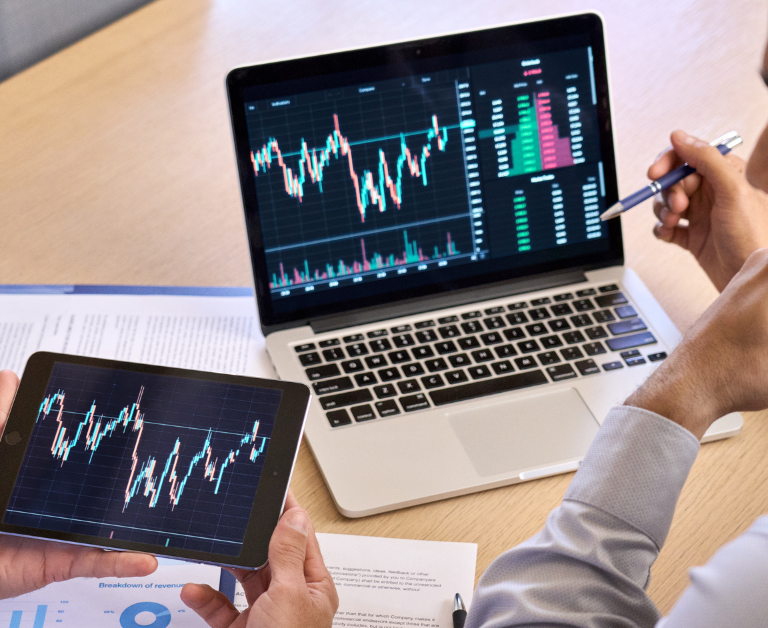
Security Best Practices for Investors, Venture Capitals, and IT Leaders
Explore strategic investments in cyber resilience by investors and venture capitals. Learn how to fortify businesses and seize opportunities for a secure future.

AI-Human Partnership Reinventing Cybersecurity Strategies: Security Best Practices
Explore the transformative synergy between AI and human expertise in cybersecurity. Learn how bug bounty programs enhance defenses against evolving cyber threats.
Cybersecurity Trends in eCommerce: A 2023 Investor’s Guide
Explore key cybersecurity trends in e-commerce, backed by numerical data. Discover how bug bounty platforms enhance investment security in 2023.
Cyber Threats Impact on Processes & Risk Management
Discover the synergy of cybersecurity and risk management. Explore innovative solutions like bug bounty platforms for proactive defense against cyber threats at BugBounter.

Seizing the Cybersecurity Goldmine: A Lucrative Investment Landscape
Unlock lucrative opportunities in the $2 trillion cybersecurity market. Explore strategic investments, bug bounty platforms, and stay ahead in this evolving landscape.
AI’s Insights Transforming Cybersecurity
Explore the transformative impact of AI on cybersecurity. From learning algorithms to bug bounty programs, discover the future of digital defense.


