Bug Bounty Tips: The Programming Foundation of Bug Bounty
Bug bounty tips shared by the BugBounter Community keeps contributing to the skills of the international community of bug bounty hunters and ethical hackers community. This week’s bug bounty tip is by Muhammad Khizer Javed. Muhammed has explained the connection between programming and bug bounty hunting. Read more below.
Being a proficient programmer is not a prerequisite for becoming a skilled hacker, but it’s definitely beneficial to have a strong foundation in programming before embarking on your bug bounty journey. Understanding coding concepts can greatly enhance your ability to identify and exploit vulnerabilities successfully. In fact, having programming skills can even help you escalate a bug from a low or medium severity to a high or critical one.
In his experience, Muhammad Khizer Javed encountered challenges during his initial bug bounty endeavors due to difficulties in comprehending code, ineffective exploitation of issues, and a lack of overall coding proficiency. He strongly recommends against bypassing the importance of programming skills when pursuing bug bounties.
Muhammad suggests gaining a basic to medium-level proficiency in specific programming languages, continuously advancing skills over time. These languages play a pivotal role in empowering bug hunters.
Python for Bug Bounty
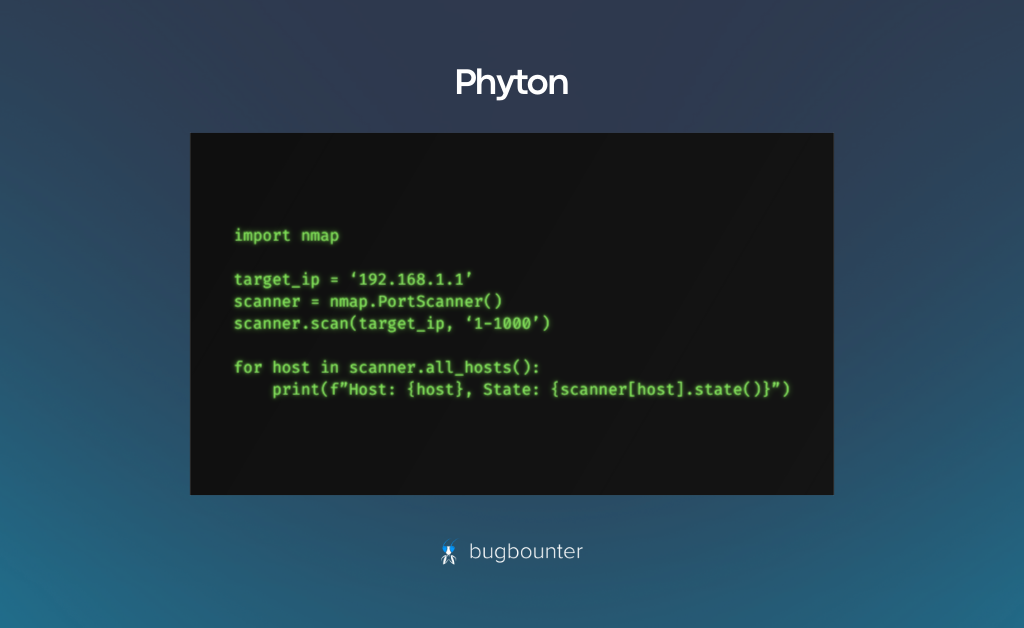
Widely used in cybersecurity, Python provides various libraries and frameworks facilitating tasks like network scanning, web scraping, and automation.
A simple Python code example using the ‘nmap’ library for vulnerability scanning is demonstrated.
JavaScript for Bug Bounty
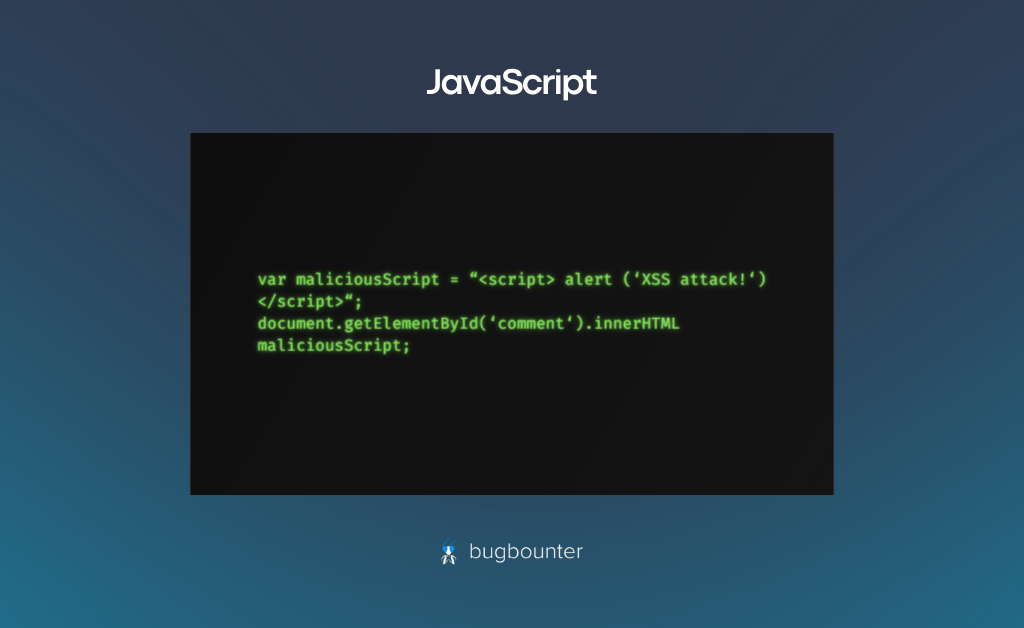
Crucial in web development, JavaScript is instrumental in identifying security flaws in web applications. Understanding concepts like DOM manipulation, secure user input handling, and detecting vulnerabilities such as Cross-Site Scripting (XSS) is essential.
A JavaScript code snippet exhibiting a simple XSS attack payload is illustrated.
Bash/Shell Scripting for Bug Bounty
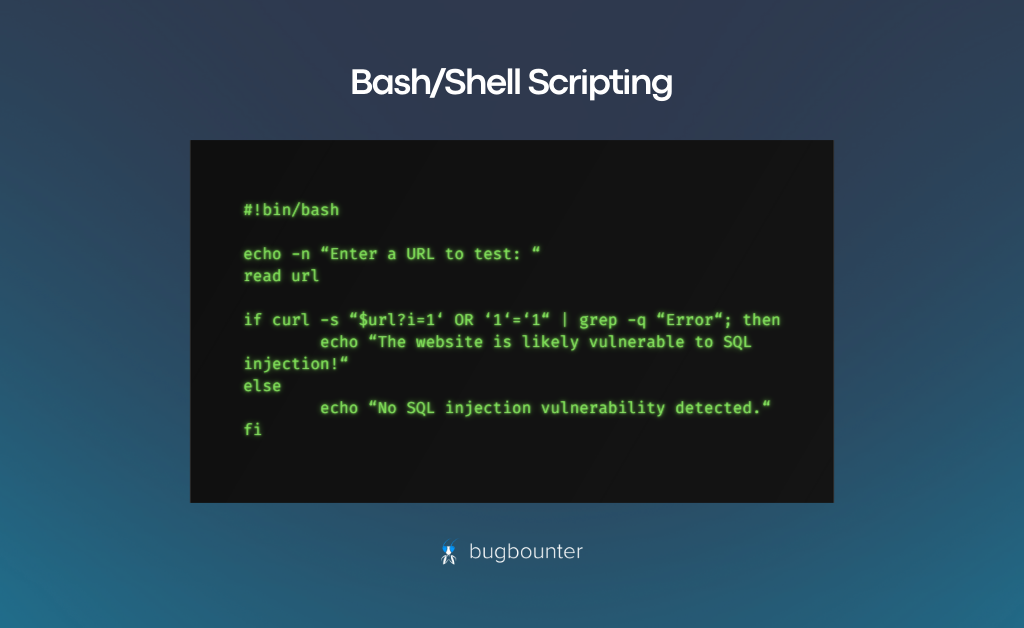
Proficiency in shell scripting aids in automating tasks, conducting reconnaissance, and creating proof-of-concepts (PoCs) for vulnerabilities.
A basic example of a Bash script automating the process of checking a website’s vulnerability to SQL injection is provided.
Continuously expanding programming knowledge and experimenting with diverse languages is crucial. It enhances bug hunting capabilities, allowing individuals to effectively discover more vulnerabilities. This constant learning and exploration significantly contribute to success in bug bounty programs.
Thank you for reading this week’s tip by Muhammad on the programming foundation of bug bounty.
Get Bug Bounty-Famous with BugBounter!
The bug bounty tips are one the most effective methods to contribute to the international community of bug bounty hunters as you help each other develop as cybersecurity researchers, and increase your online reputation.
BugBounter values the efforts of the bug bounty hunters who’d like to contribute to the international community of bug bounty hunters at the utmost level.
If you are not registered on BugBounter, register today and reach out to us with the following:
- Your BugBounter username,
- A photo of you, or a display picture to represent you,
- The social medias you’d like to be tagged with your username,
- And – the most important one – your bug bounty tip.
Please note: your bug bounty tip might be altered according to our bug bounty tip style guidelines. We will ask for your approval before publishing the bug bounty tip.





