BugBounter Cybersecurity Newsletter | August 2023
Hello there,
Check out this month’s cybersecurity newsletter for getting updated in no time.
Stats from BugBounter
Check out the distribution of the vulnerabilities and their severities on BugBounter.
Top Vulnerabilities Identified on BugBounter in August 2023
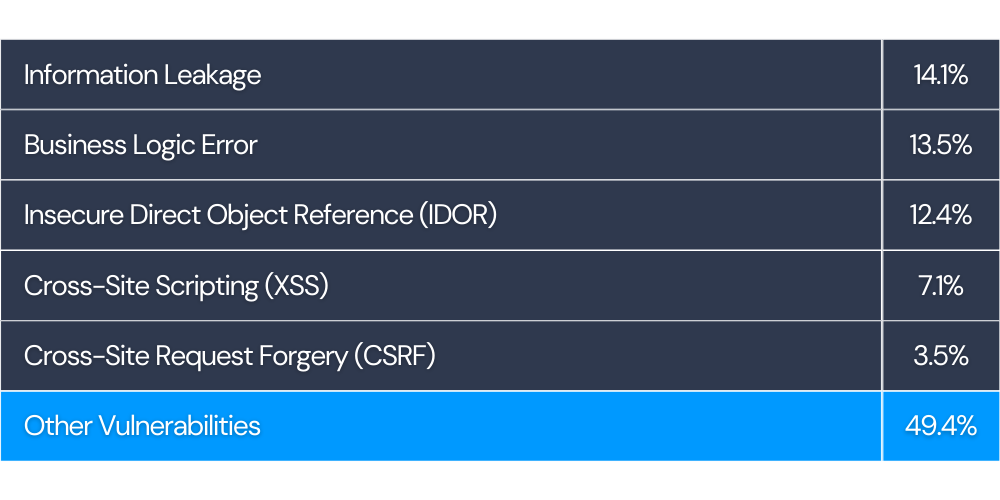
The data above shows that information leakage, business logic, and IDOR require attention for a strong cybersecurity posture (BugBounter data between 1-31 August, 2023).
Distribution of Severity (CVSS) of the Reports in August 2023
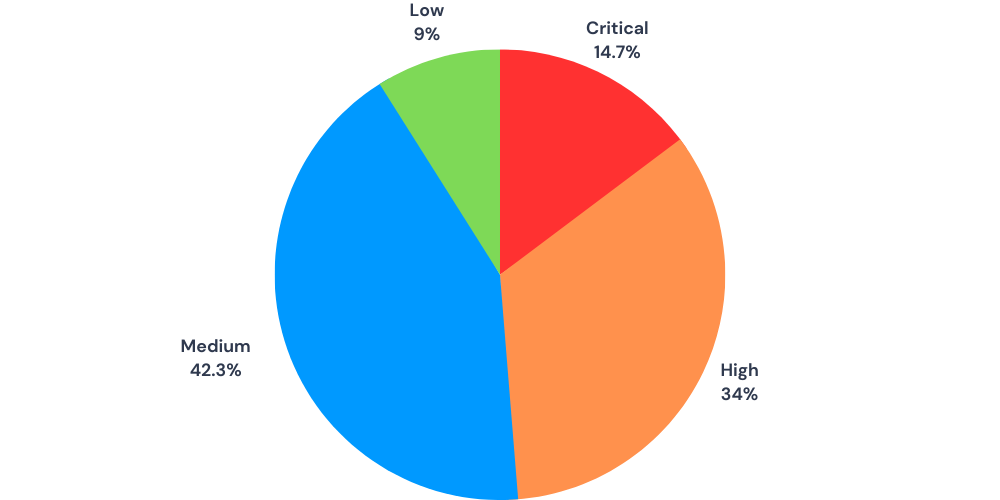
High and Medium risk findings predominate, constituting over 75% of identified issues. Prioritizing these vulnerabilities is crucial for robust cybersecurity (BugBounter data between 1-31 August, 2023).
August 2023 Threat Landscape: Explained Briefly
BugBounter sheds light on the current cybersecurity landscape in August 2023. Explore the latest cybersecurity incidents from around the world, based on real-time cybersecurity news. Read the article.
Keep Your Business with BugBounter Cybersecurity Tips
CISO
Bug bounties provide real-world testing, amplifying threat visibility and fortifying your digital airspace.
Researcher
Reward money is not our first motivation to find a vulnerability, but it definitely helps to stick to a program.
BugBounter
Bug bounties offer effortless and effective vulnerability detection. Elevate protection with user-friendly testing.
Read the Latest BugBounter Cybersecurity Articles

The Human Element in Cybersecurity: Archiving the Tech-Awareness Balance
Discover the pivotal role of human expertise in cybersecurity testing. Striking the tech-awareness balance for robust cyber defenses. Read here.

Elevating eCommerce Security: Navigating the Digital Landscape
Elevate eCommerce security with BugBounter’s bug bounty platform. Uncover the power of human expertise in cybersecurity. Read here.
Thank You for Reading
BugBounter invests in human intelligence as a cybersecurity for companies, regardless of their industries and sizes. Go to our Solutions page for learning more.