Unlock bug bounty success and high bounty rewards with Bug Bounty Talk, powered by BugBounter! Join us for insights, Q&A, and networking. Arrange an event now.
Bounters’ Newsletter (March 2023)
Bounters’ Newsletter (March 2023)
Hey there Bounters,
We’re hoping that you’re doing great. After the earthquake disaster we experienced last night, we had to leave our routine to focus on helping the victims and rescue & aid teams in reaching donations and information securely. We appreciate the hard work of all ethical hackers who supported us during this difficult process.
🏆 March Top 10
| 🥇 erste | 6. GMG |
| 🥈 ogoktas14 | 7. khaganyk |
| 🥉 gwetri | 8. hemanthjoseph |
| 4. ekbereksi | 9. mnykmct |
| 5. mygconsole | 10. alp |
💡 Don’t see yourself on the list? Start hunting now to take place in the next month’s list!
👾 Join Discord
Communication is the key (wow, cheesy). That’s why we started our own Discord Server for our Community Members to stay in touch, exchange info, and chat!
Bug Bounty Talk with Nigde Omer Halisdemir University
Unlock bug bounty success and high bounty rewards with Bug Bounty Talk, powered by BugBounter! Join us for insights, Q&A, and networking. Arrange an event now.
Bug Bounty Talk with Ege University
Unlock bug bounty success and high bounty rewards with Bug Bounty Talk, powered by BugBounter! Join us for insights, Q&A, and networking. Arrange an event now.
Bug Bounty Talk with Mersin University
Unlock bug bounty success and high bounty rewards with Bug Bounty Talk, powered by BugBounter! Join us for insights, Q&A, and networking. Arrange an event now.
Bug Bounty Talk with Istanbul Technical University
Unlock bug bounty success and high bounty rewards with Bug Bounty Talk, powered by BugBounter! Join us for insights, Q&A, and networking. Arrange an event now.
Bug Bounty Talk with IEEE Canakkale On Sekiz Mart University Student Branch
Unlock bug bounty success and high bounty rewards with Bug Bounty Talk, powered by BugBounter! Join us for insights, Q&A, and networking. Arrange an event now.
Bug Bounty Talk with Gebze University
Unlock bug bounty success and high bounty rewards with Bug Bounty Talk, powered by BugBounter! Join us for insights, Q&A, and networking. Arrange an event now.
Bug Bounty Talk with Yeditepe University
Unlock bug bounty success and high bounty rewards with Bug Bounty Talk, powered by BugBounter! Join us for insights, Q&A, and networking. Arrange an event now.
New Year, New Me… And New Cyber Security Solutions | BugBounter Newsletter
🏡 News from BugBounter
2022 Reflections of our Team and Community
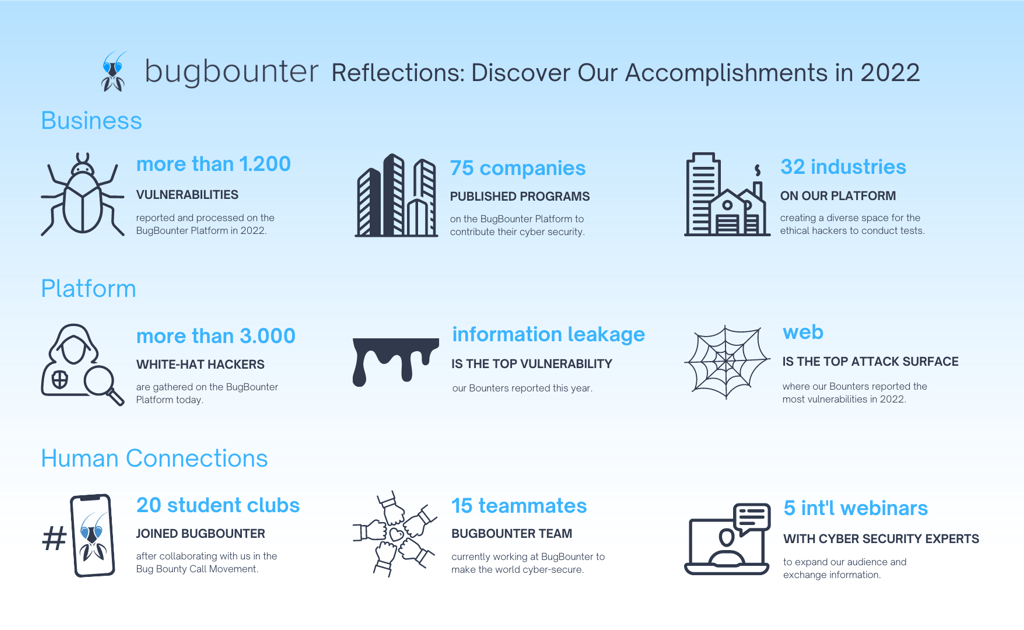
It is safe to say, both as a startup and a community, BugBounter made significant progress in 2022. From collaborating with new partners to growing our ethical hacker community through the events we held, we grew and learned so much. We’re looking forward to using what we’ve learned and experienced in 2022 to revolutionize the cyber security methods of today.
🌍 News from the Cyber Security World
“Twitter Denies Hacking Claims and Theft of 200 Million Users’ Email Address”

Twitter Inc. undertook a thorough investigation in response to recent media claims that the data of 200M Twitter users were being sold online, and the results suggest that there is no proof that the data that was recently sold was obtained by exploiting a flaw in the Twitter systems. (Source: Cyber Security News
“Britain’s Postal Service, Royal Mail Suffers Cyber Attack”

“An incident involving a cyber attack has caused severe service disruptions at Royal Mail, the British postal service and courier company. In the absence of any further details, it is not known what the nature of the incident was.” (Source: Cyber Security News)
💡 Cyber Security Tip
This month BugBounter Team has a tip for your company to avoid cyber risks:
“It’s important to remember that cybersecurity is a constant battle. No single strategy will be able to protect you from malicious hackers forever—you have to keep up with them as they develop new techniques and improve on old ones. Be a better malicious hacker than the actual ones.”
📌 BugBounter Blog
Cyber Security in Retail and eCommerce Industries

Retail and eCommerce companies are hot targets for the cyber criminals. What is the best way for them to protect their business and brand value, is bug bounty a convenient method for them?










