Bug Bounty Tip: File Analysis & Session Manipulation in Mobile App Testing | BugBounter
Ömer Göktaş, one of the top cybersecurity experts in the BugBounter Community shares a bug bounty tip you can all benefit from while testing mobile apps.
When conducting mobile app testing, after completing the final testing phase, it’s crucial to shift focus to scrutinizing the app’s native files for potential vulnerabilities. Begin by thoroughly analyzing all files, paying special attention to those related to user sessions.
For enhanced testing, consider utilizing the following steps:
Step 1: File Examination
Use a disassembler tool like apktool to dissect the APK file. Look for any sensitive information or configuration files.
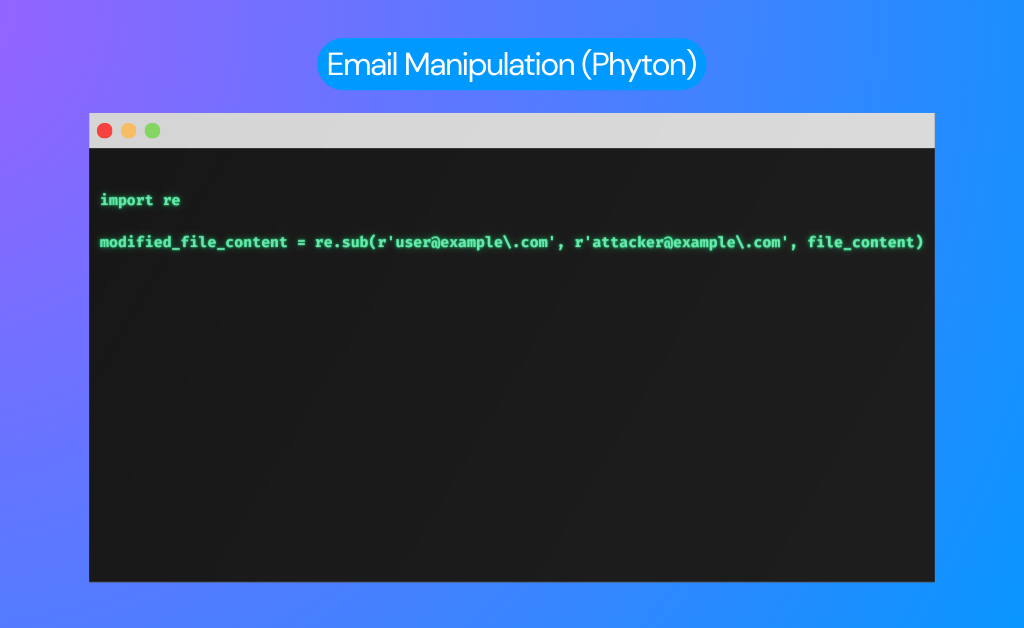
Step 2: Email Manipulation
Within session-related files, identify email addresses and modify them. For instance, using Python:
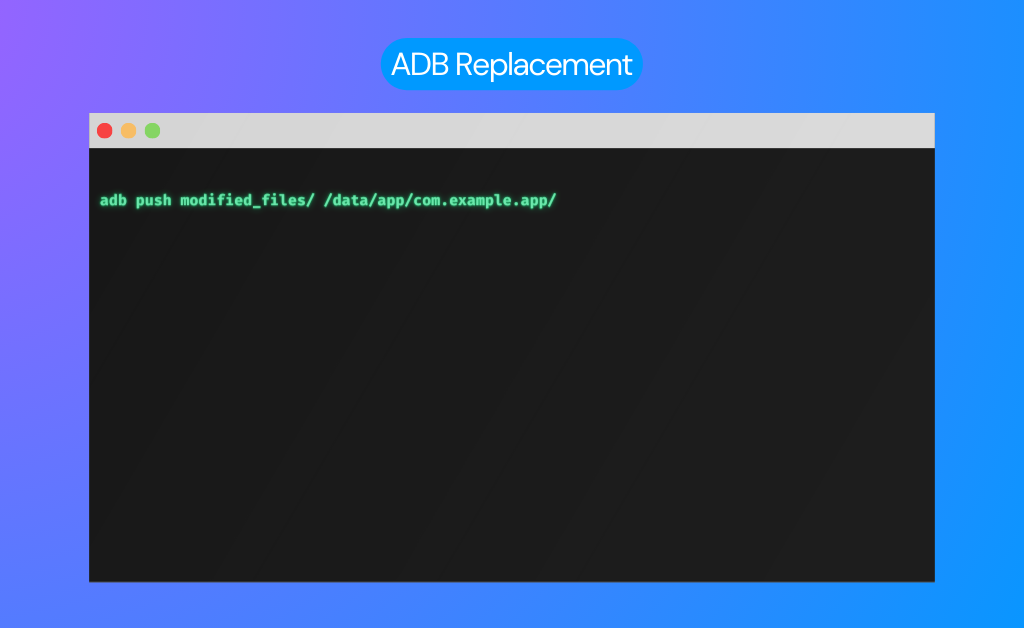
Step 3: ADB Replacement
Before launching the app, overwrite the existing files with modified ones using ADB commands.
Step 4: User Impersonation
With luck, the app might load with a different user’s session, exposing potential authorization issues.
Thank you for Reading
We thank Ömer Göktaş for this week’s bug bounty tip. If you’d like to be featured on Bugbounter social medias with your bug bounty tip, don’t hesitate to reach out to us. Let’s help each other improve!
For more bug bounty tips like this, go to our Community Page.





